How to Configure Firewall Rules
DigitalOcean Cloud Firewalls are a network-based, stateful firewall service for Droplets provided at no additional cost. Cloud firewalls block all traffic that isn’t expressly permitted by a rule.
Inbound firewall rules define the traffic allowed to the server on which ports and from which sources. If no inbound rules are configured, no incoming traffic is permitted.
Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. If no outbound rules are configured, no outbound traffic is permitted.
Add, Update, or Remove Rules from a Firewall Using the CLI
The firewall rule management commands require the firewall’s ID. To retrieve a list of firewalls and their IDs, use the doctl compute firewall list command.
Add, Update, or Remove Rules from a Firewall Using the API
The firewall rule management calls require the firewall’s ID. To retrieve a list of firewalls and their IDs, use the /v2/firewalls firewalls endpoint.
Add or Remove Rules from a Firewall Using the Control Panel
To manage a firewall’s rules, navigate from Networking to Firewalls. Click the firewall’s name to go to its Rules tab. From here, you can create new rules and edit or delete existing rules.
Create New Rules
You can create new inbound and outbound rules by opening the New rule select list under Inbound Rules or Outbound Rules, respectively. You can use a preset protocol or create a custom rule.
X-Forwarded-For, Content-Type, or User-Agent.From Presets
There are several common protocols available which will fill the Protocol and Port Range fields automatically. For example, selecting HTTP will auto-fill the Protocol with TCP and the Port Range with HTTP’s default of port 80.
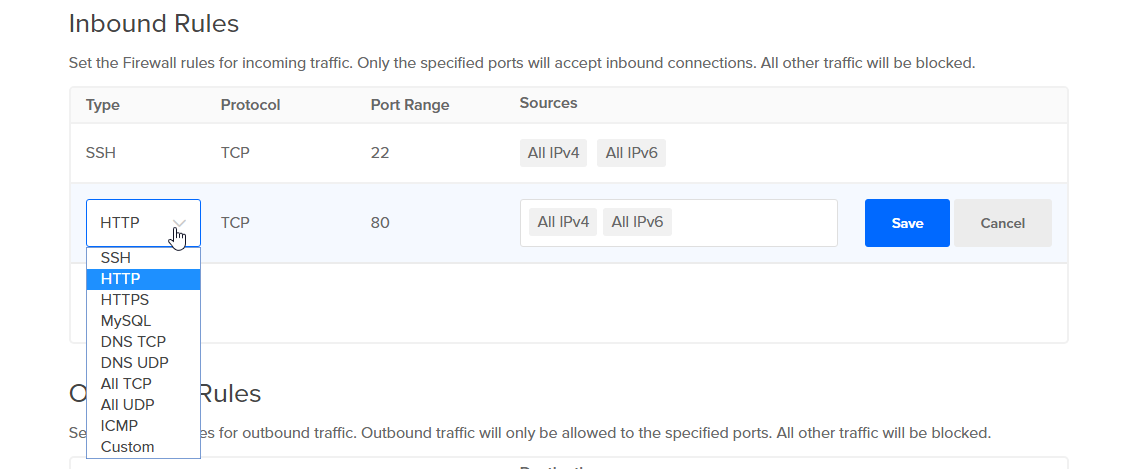
If one of these services is listening on a non-standard port, you can configure it by creating a custom rule.
Custom Rules
To add a custom rule, choose Custom, which allows you to define the protocol, port range, and source or destination.
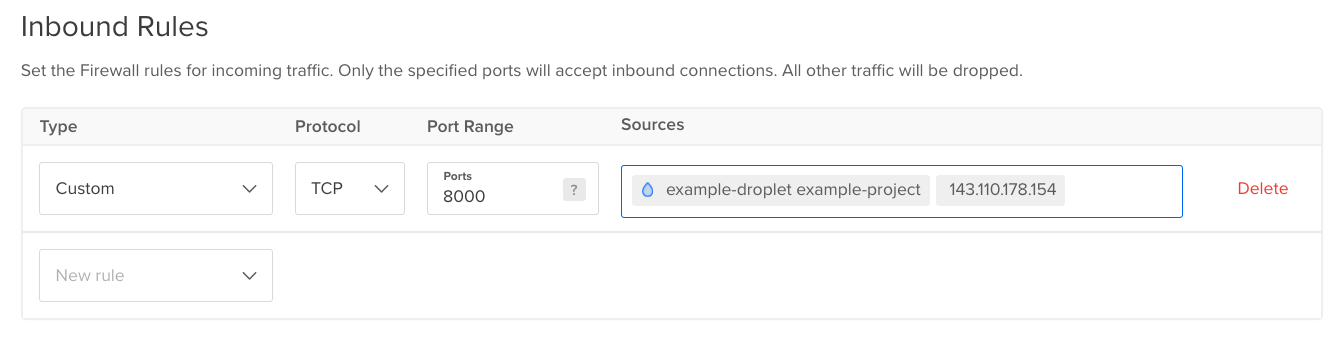
For a custom rule, specify the:
-
Protocol. You can choose either TCP or UDP. Because ICMP has no port abstraction, to allow ICMP traffic, you select it directly from the New rule dropdown.
-
Port Range. For the TCP and UDP protocols, you can specify:
- A single port.
- A range of ports by entering the starting and ending ports separated by a dash
-with no spaces, such as3000-4000. To open multiple non-sequential ports, create a separate rule for each. - All ports by leaving the field blank.
-
Sources for inbound rules, which lets you restrict the source of incoming connections. You can restrict incoming connections to:
- Resources or tags by entering the name of the resource or tag. This includes Droplets, VPCs, Kubernetes clusters, resource tags, load balancers, and IPv4/IPv6 addresses.
- IP addresses or IP ranges by entering individual IP addresses or entering a CIDR. For example, enter the CIDR 10.128.0.0/16 to a rule allows incoming traffic from any IP address between the 10.128.0.0 and 10.128.255.255. The same properties applies to IPv6 addresses and CIDRs.
- Types of IP addresses by choosing All IPv4 or All IPv6 in the sources field. This allows all IP addresses of a specific type (either all IPv4 addresses or all IPv6 addresses) to connect to the Droplet. If you are using the API, enter
0.0.0.0/0(IPv4) or::/0(IPv6) into theaddressesfield of thesourcesobject to allow incoming traffic from a specific type of IP address.
-
Destinations for outbound rules, which lets you restrict the destination of outgoing connections.
You can limit the sources/destinations to:
- Droplets, chosen by name, IP address, or tag
- DigitalOcean Load Balancers, chosen by name, IP address, or tag
- DigitalOcean Kubernetes clusters, chosen by name, or tag
- Non-DigitalOcean servers by IP addresses, subnets, or CIDR ranges.
Edit or Delete Rules
To edit or delete a rule, open the rule’s More menu:
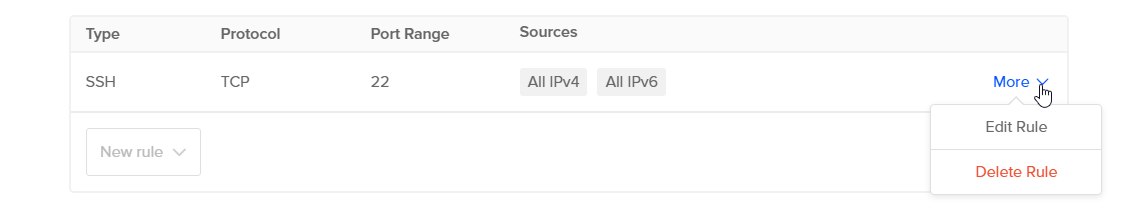
Choose Edit Rule or Delete Rule. When you select Delete Rule, the rule is deleted immediately without an additional confirmation prompt.