Use VPC Networks to Secure Your Servers and Other Best Practices
A Virtual Private Cloud (VPC) is a private network interface for collections of DigitalOcean resources. VPC networks are inaccessible from the public internet and other VPC networks, and traffic on them doesn’t count against bandwidth usage.
While developing your systems and applications, you should build your infrastructure as securely as possible to avoid bad actors from compromising your infrastructure. This guide outlines how to implement VPC and other best security practices to help you develop secure infrastructure.
Isolate Environments and Tenants with VPC Networks
VPC networks allow you to better secure execution environments, tenants, and applications by isolating resources into networks that can’t be reached by the public internet. This keeps your resources organized and keeps access to them limited to other resources in the VPC network. This can also boost privacy for tenants using your applications.
Isolate Execution Environments
A common implementation is to create a VPC network for each of your development, staging, and production environments. This would mean replicating your application’s web servers, databases, and storage volumes across three separate VPC networks and then safely deploying your application changes to each subsequent environment.
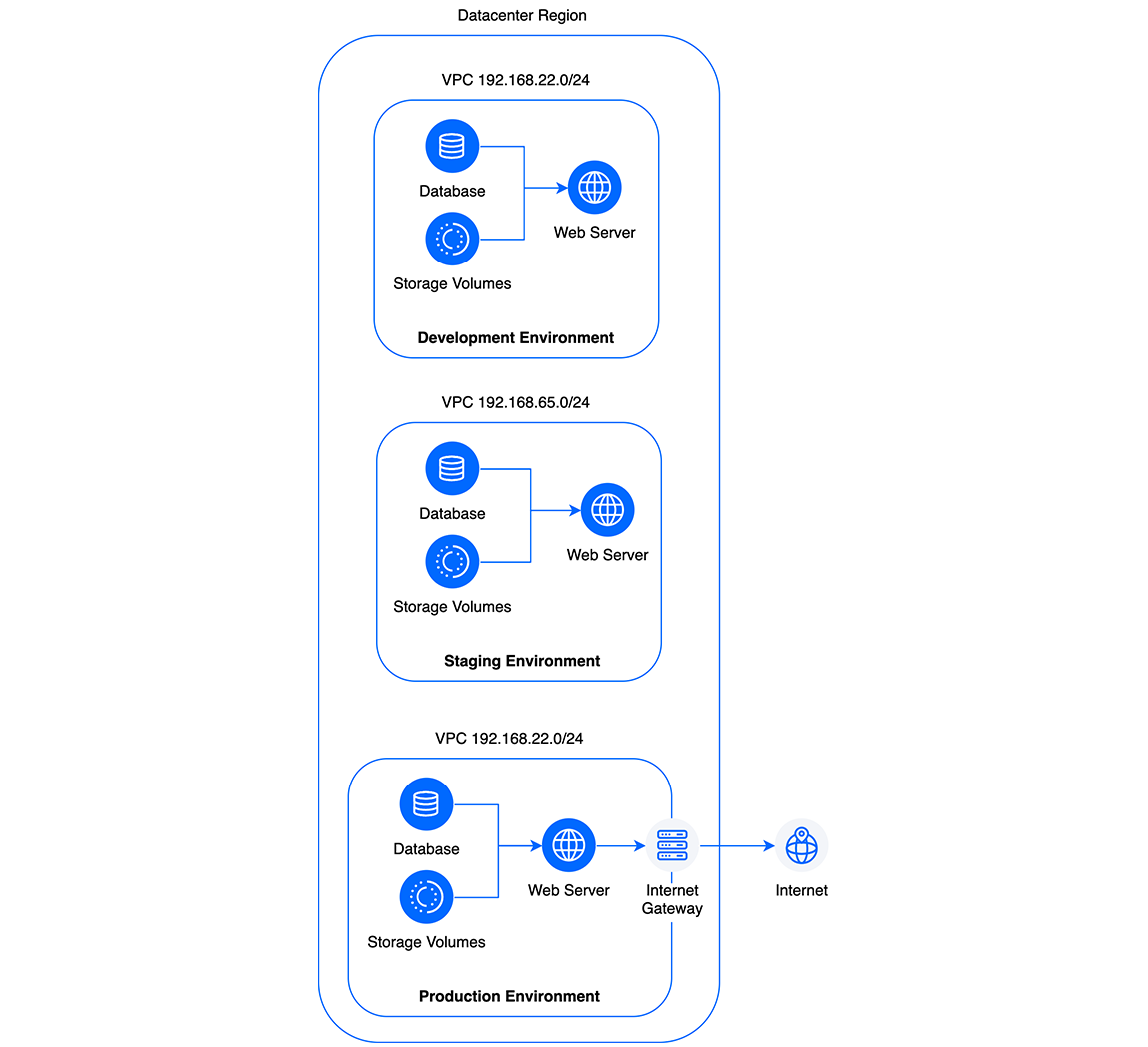
Isolate Tenants
VPC networks also allow you to isolate different tenants (customers) from one another by separating them into each of their own VPC networks. Isolating tenants to their own VPC network keeps their resources secure from other tenants from connecting to their resources by mistake and avoids privacy issues.
This network diagram illustrates how tenants’ environments could be isolated. The internet gateways in each tenancy are optional.

SSH Keys
SSH keys are cryptographic keys that can be used as credentials to access your Droplets using an encrypted connection. Each set of keys contains one public and one private key: the public key residing on the Droplet being accessed, and the private key residing on the device accessing the server.
Because SSH keys contain more bits of data, they are significantly more difficult to compromise than traditional passwords. Establishing SSH keys allows you to safely disable password-based authentication to your Droplets.
How to Implement SSH Keys
You can add SSH keys when you create new Droplets or add SSH keys to existing Droplets.
Cloud Firewalls
Cloud Firewalls provide an additional layer of protection between your DigitalOcean resources and the public internet. They allow you to define which types of connections are allowed to connect to your Droplets and what services are exposed on them. You can configure them to restrict access to specific ports on your Droplet or block specific types of connections, such as SSH or SMTP connections.
On your Droplet, a number of services are running by default, which you can categorize into the following groups:
- Public services can be accessed by anyone on the public internet, such as your personal blog or company website.
- Private services can be accessed by a select group of authorized users, such as a database.
- Internal services should only be accessible from within the server itself, such as databases that only accept local connections or server logs.
You can configure cloud firewalls with varying layers of granularity to filter traffic to your Droplet’s services, such as only allowing inbound SSH connections from a specific range of IPs to your Droplet. These are called rules. Each firewall can have up to 50 total incoming and outgoing rules. A DigitalOcean Cloud Firewall can protect a maximum of 10 individual Droplets. A cloud firewall can protect more than 10 Droplets if the firewall is applied to an entire tag of Droplets.
How to Implement Cloud Firewalls You can create and apply cloud firewalls using the DigitalOcean Control Panel or API. You can also use third-party firewall software on your Droplets, such as UFW, iptables, or CSF, but they require some manual configuration. See our community tutorials on how to set up third-party firewall software:
- How To Setup a Firewall with UFW on an Ubuntu and Debian Cloud Server
- How To Set Up a Firewall Using Iptables on Ubuntu 14.04
- How To Install and Configure Config Server Firewall (CSF) on Ubuntu
Service Auditing
Service auditing is the practice of regularly reviewing the services running on your infrastructure to ensure that they are supposed to be running on your system and are behaving correctly. Often, the default operating system is configured to run certain services at boot. Installing additional software can sometimes pull in dependencies that are also auto-started. Each service running on your servers is an increased opportunity for malicious attackers to compromise your infrastructure. As you run more services on a server, you need to update more to keep your services security compliant.
How to Implement Service Auditing on Your Droplet
You can audit your Droplet’s services several different ways. The netstat tool is one option, but you can use other networking tools to develop a regimen that works for you.
netstat returns a list of services currently running on your machine, the ports they are using, and the types of connections they are making to other resources in your network or on the internet:
sudo netstat -plunt
You will see output that looks like this:
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 887/sshd
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 919/nginx
tcp6 0 0 :::22 :::* LISTEN 887/sshd
tcp6 0 0 :::80 :::* LISTEN 919/nginx
The most important columns are Proto, Local Address, and PID/Program name. If the address is 0.0.0.0, then the service is accepting connections on all interfaces. If you do not recognize the a service that is running on your server, research its purpose and whether it belongs on your server.